This article provides a reference setup of an ATSEP cybersecurity infrastructure, based on SkyRadar's ATSEP Cybersecurity Training Module. The main goal is to familiarize students with the most dangerous type of possible attacks, and teach possible countermeasures.
The ATSEP skill set can be categorized according to ICAO's Doc 10057 into the following competency elements:
- Engineering
- Situation Awareness
- Service Provision
- Coordination
- Management of non-routine Situations
- Problem Solving and Decision Making
- Self-Management and Continuous Learning
- Workload Management
- Teamwork
- Communication
The cybersecurity skills actually blend into most of these fields. We should not reduce them on a pure Software Management task. It requires competencies in engineering, but also rapid strategies to gain situation awareness in cases of attacks, team work, targeted communication, and trained escalation routines for non-routine situations.
Technically it also spreads along the sectors
- Aeronautical Information Services
- Meteorological infrastructure and subsystems
- Voice and data communication systems
- Navigation systems
- Surveillance systems
- Data processing and data automation
- Monitoring and Control Systems
So the skill-set needs to be technical (cognitive), procedural and social/interpersonal.
SkyRadar's solution below has been conceived based on
- the competence and skill building requirements
- typical ATM infrastructure
- lessons learnt from establishing cyber security in industry sectors like banking and finance.
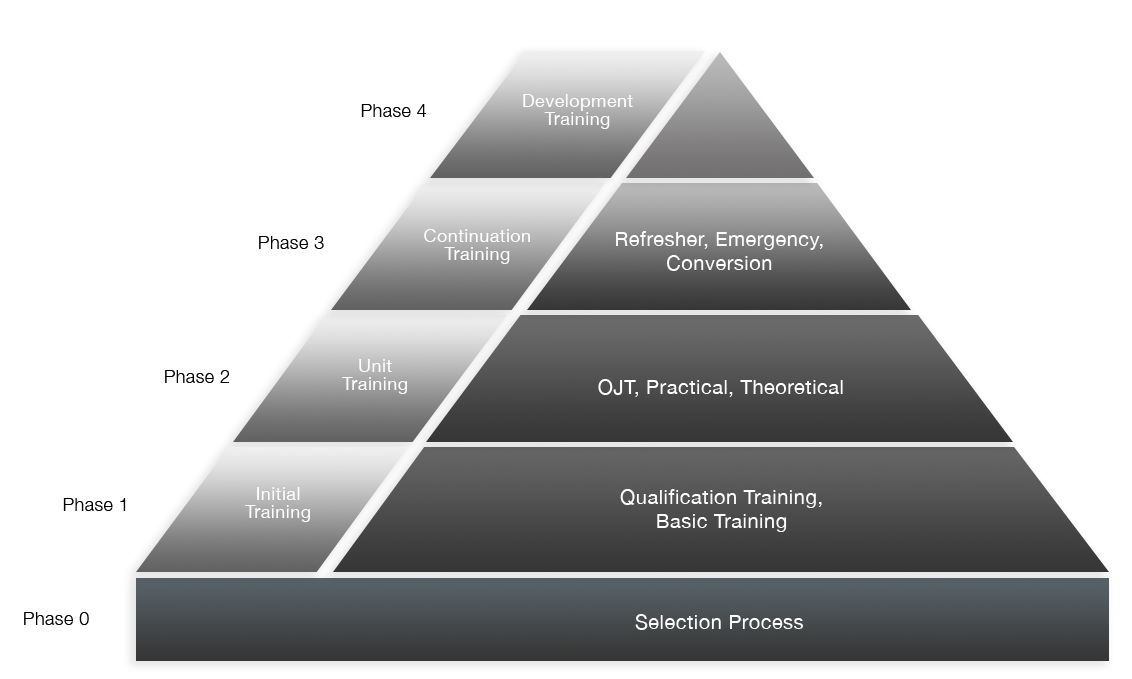
Cyber-security training should be supplied based on the required skill-set during all phases of the ATSEP's Competency Based Training and Skill Building journey.
Training System setup
The training infrastructure includes the following
- RADAR 1 (real training Pulse Radar)
- RADAR 1 (included computer with Radar DSP)
- RADAR 2(SSR - simulated)
- Radar 2 (included computer with Radar DSP)
- ADS-B receiver (real device)
- ADS-B(included computer with Radar DSP)
- a) Managed switch with L3 capabilities. We use the CISCO Catalyst 24 ports . With the 99 % of probability students will meet the same vendor in a real airport. See appendix 1 for requirements.
b) Message Queue server. This is a typical infrastructure which we find in decentralized service-oriented architectures. - RADIS server (possibly VM)
- Attacking station (see description below)
- MS standalone Certification Authority CA (easiest) or Linux with XCA
- RADAR cloud servers providing external data
- Student workstation with FreeScopes.
All equipment, for simplicity, connected to the same physical commutator - CISCO Catalyst.
Possible usage scenarios
Fake RADAR
Attack
- The system works as usual - RADARs emit data to RADIS and then - to server and WS
- The trainer runs the fake RADAR sending some valid ADS-B data to RADIS
- RADIS is not able to distinguish real and fake.
- Students see a ghost airplane in FreeScopes
Possible countermeasures
- Implement port security on managed switch (reject traffic from attacking machine)
- Setup firewall rule on L3 on firewall rule (why we need CISCO)
- Implement IPSEC connection from a RADAR mgmt machine to RADIS
- Isolate attacking machine in separate VLAN
RADIS crash
Attack
- System works as usual
- Trainer runs exploit software
- RADIS crashes and stops working
- No data will be seen on WS
Countermeasures (possible)
- Install newer version of RADIS
- Make sure exploit does not work anymore
Workstation suppression
Attack
- System works as usual
- Trainer runs DOS attack targeting student’s WS
- WS stops working, no data is displayed
Countermeasures
- Tune WS iptables firewall - reject DOS traffic
- Find attacking machine MAC or IP and make rejecting rule on Switch
- Isolate attacking machine in VLAN
ADS-B data eavesdropping
Attack
- System works as usual
- Trainer runs on attacking machine Wireshark and monitor and read ADS-B data (and not only)
Countermeasures
- Isolate attaching machine in VLAN
- Implement IPSEC from RADAR mgtm to WS (using PKI and CA)
Equipment required
- SkyRadar's NextGen 8 GHz Pulse radar, SSR-Simulator and the ADS-B training unit
- One physical server with HyperV (say) or VMWare or Xen or docker installed (need to think)
- Managed L3 switch - CISCO Catalyst is recommended (with L3 capabilities).
- Computers operating FreeScopes
- SkyRadar's CloudServer to operate the Message Queue
Skills required
Some terminal software usage experience. Linux bash, CISCO console are very helpful.
Otherwise it should be integrated as Module 0 into the Cyber Security Training plan.
Next Steps
Talk to us for your requirements on the Cyber Security Training Infrastructure. We can adapt the infrastructure on your skill requirements and if required, supply it integrated in a complete Radar & Tower Simulator, based on an operational ATM system.
Our trainers can provide intensive train-the-trainer seminars in your location in various languages.
About the Authors
 Peter Smirnoff has a long experience in Cryptography, both in industry and research. Peter has worked on the Windows Crypto API, OpenSSL, digital signatures, X 509 Certificates etc. He has profound implementation experience with PKCS-11 smart-cards as well on Linux and Windows platforms. Ulrich Scholten is cofounder of SkyRadar. As a research associate at the Karlsruhe Service Research Institute, he researched network effects, emergence and control mechanisms in platforms and distributed cloud scenarios. He holds several patents related to radar technology and the Internet of Things. Ulrich has a PhD in Cloud computing.
Peter Smirnoff has a long experience in Cryptography, both in industry and research. Peter has worked on the Windows Crypto API, OpenSSL, digital signatures, X 509 Certificates etc. He has profound implementation experience with PKCS-11 smart-cards as well on Linux and Windows platforms. Ulrich Scholten is cofounder of SkyRadar. As a research associate at the Karlsruhe Service Research Institute, he researched network effects, emergence and control mechanisms in platforms and distributed cloud scenarios. He holds several patents related to radar technology and the Internet of Things. Ulrich has a PhD in Cloud computing.