Air Traffic Management (ATM) systems support aircraft in their transition from departure to destination. Given their strategic importance to societies and economies, they are an appealing target for cyber threat actors.
Reasons could be for personal or political gain. Here we look at how technology and digitization provide numerous benefits to aviation while also posing challenges in addressing cyber threats within this complex environment.
The ATM system consists of a range of physical, organizational, informational, as well as human assets that interact in a complex ‘system of systems’. In turn, this delivers a seamless traveling experience to passengers that they have come to expect. Operational stakeholders include Air Navigation Service Providers (ANSPs) and the EUROCONTROL Network Manager (NM), working together to deliver air traffic flow and capacity management (ATFCM).
|
This diversity of systems has major consequences for cybersecurity. Cybersecurity risks have the potential to disrupt operations and cause considerable financial harm to airlines and airports. Each system or ‘node’ should have its own protocol for data transport and storage. |
The ATM system is a mix of interconnected systems made up of bespoke legacy systems. In many instances, these are commercial off-the-shelf systems linked via a variety of interfaces that are based on a combination of national, international, and proprietary standards, navigation and surveillance (CNS) systems, ground and space-based communication, air traffic control centers (ACCs), airports, and the information used by and shared between systems as aircraft are assisted through controlled airspace are all examples.
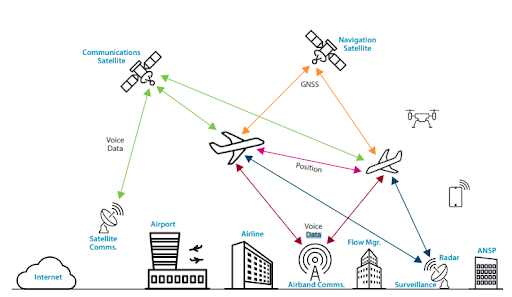
Figure: Interconnected dataflow in Air Traffic Control, Source: Eurocontrol
There are numerous communication protocols and techniques used between air-to-ground and air-to-air. These contain a collection of data such as aircraft communication data, voice information, and flight planning based on specific protocols. All radar detection and chasing systems, including air defense and army elements, use identical tactics.
Each component within this system requires its own security, which has a requirement to be implemented using valid and established methods.
Introducing Public Key Infrastructure
The aviation sector, like the automobile industry, has a very complicated supply chain. Strong authentication and secure communication for devices and systems have a requirement to be enabled by purpose-built Public Key Infrastructure (PKI) for IoT. Using PKI-based authentication inhibits communication from unauthorized components or devices, hence preventing a wide range of threats.
A Public Key Infrastructure (PKI) is critical in establishing a trustworthy and secure aviation environment by being able to verify and exchange data between multiple entities which can be users, networks, applications or devices. The purpose of a PKI is to create a trusted environment for all entities that are connected. PKI works through the implementation of two technologies: digital certificates and cryptographic keys.
With PKI, IoT entities can enable direct authentication across systems in a decentralized handling of authentication. While not vulnerable to common brute-force or user-deception attacks, PKI enables the secure storage and transmission of sensitive information. This protects it from malicious actors even if a data stream or data source is intercepted or hacked.
Security in the SkyATSEP need to learn how to protect ATC infrastructure to withstand the growing threat of cyberattacks on the aviation sector. EU Regulation 2017/373 explicitly mandates cybersecurity infrastructure and processes. Speak with the SkyRadar team about training infrastructure for ATSEP related technical training |




