Gartner's 2021 report on cyber security was published just now. And it shows important trends in cybersecurity. This article discusses the implications for ATC cybersecurity and ATSEP qualification and training needs in particular.
Increasingly Networked Infrastructures for increased operational effectiveness
Pre-Pandemic
Before the COVID-19 pandemic, organizations around the globe were already rapidly opening up their infrastructures. Air Traffic Management & Control integrated decentral units and devices into digital value networks, embracing hybrid cloud structures and creating enhanced "composite services" through the orchestration of own and third party services. A good example is the IATA's eCargo process and the Cargo iQ Master Operating Plan, integrating the complete airflow value chain, including airlines, forwarders, shippers, consignees, customs, cargo handling agents etc.
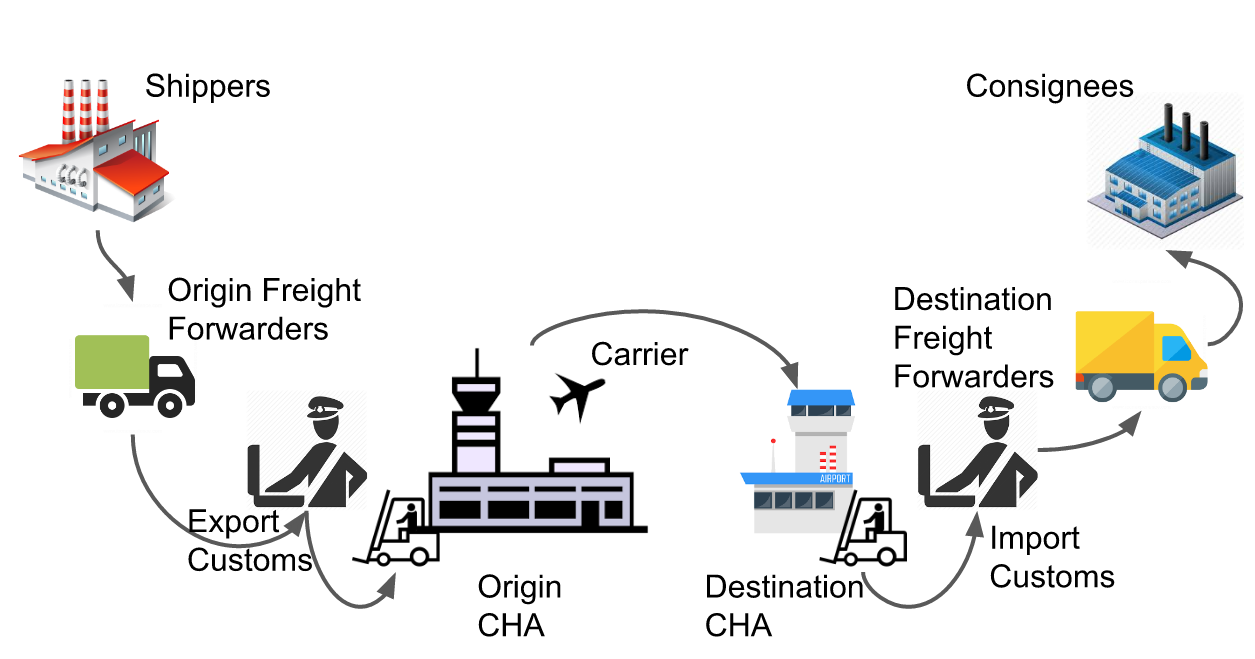
Figure: The eCargo Process
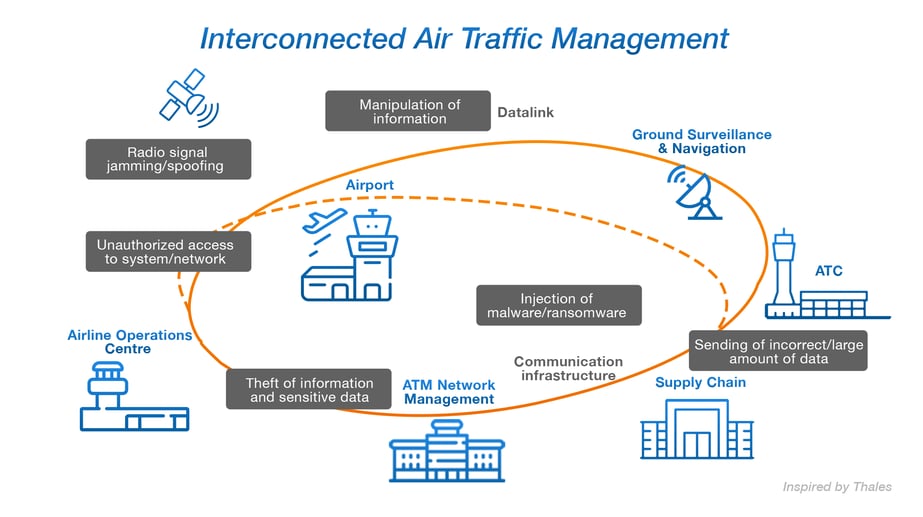
In air traffic control the whole monitoring and surveillance infrastructure is a digitally connected decentralized infrastructure with many flanks for third party intrusion. Peripheral sources like primary radars, secondary radar sources like MSSR, ADS-B or whole MLAT networks, external sources like flight or weather data, networked information from other control centers or airline operation centers all enter the ATM network.
Figure: Interconnected Air Traffic Management (inspired by: Thales)
The Pandemic as Accelerator of Change
Once the pandemic hit, it became glaringly apparent that from now on, doing business would be anything but normal as a new normal took shape. Now industries, including the aviation sector, acknowledge that to keep security risks at bay, they must adopt a 24/7 defensive posture to elevate cybersecurity and fully understand the risks to their business as the insurgence of remote users continues.
Looking at Gartner's 2021 Top Security and Risk Trends
Cybersecurity has always been a critical concern for the aviation sector in keeping the airways safe for passengers and crew alike. In what follows, we will discuss the top security and risk trends for 2021 as identified by Gartner.
There are important implications of these trends for ATSEP qualification of the industry’s current and future technical specialists. ATSEP includes engineers, technicians, and computer software and hardware specialists responsible for specifying, procuring, installing, calibrating, maintaining, testing, and certifying ground electronic systems used in the safe control of aircraft movement.
Trend #1: Cybersecurity Mesh
While many organizations had begun, or were just beginning their digital transformations pre-COVID-19, the pandemic accelerated digital business. The trend today is that many digital assets and employees, are working outside the confines of the traditional enterprise structure. Therefore, there is an increased need for security options that are agile, flexible, composable, and scalable that will help organizations move forward in a secure manner.
The ATC infrastructure is strongly decentralized. Parts of the system belong the the realm of the ANSP, like the radars, the Towers (including central systems like RDPS or SDPS), APP and ACC infrastructure. Here security can be centrally managed, including Public Key Infrastructures, secured by central policies, key management, security management and audits. But it also embraces third party data, like data coming and going to the airports, the aircraft, from other ANSPs and third parties. Here, trustworthy digital identities, secure authentication and encrypted communication are important.
The ATSEP has to understand the various systems and to be aware of potential attack scenarios, so that in case of an attack, the correct escalation routine can be executed.
Trend #2: Cyber-savy boards
With numerous high-profile and very public security breaches, boards are paying more attention to cybersecurity matters. They see the enormous risk cyber attacks present to their enterprise. Therefore, many boards are now forming committees that are focused on discussing cybersecurity issues. These committees are typically led by a member with cybersecurity experience or a third-party consultant. CISO’s in such organizations can expect increased scrutiny and expectations, but the bright side is that they should also be seeing an increase in support and resources.
Foresightful companies set up a Security Operations Center (SOC), which continuously monitors the infrastructure. In cases of alerts, a second team, the Computer Emergency and Rescue Team (CERT) has to eliminate the threat. Given the rising amount of "personalized" attacks on infrastructure, including well researched phishing, even this is not sufficient anymore to protect the Air Traffic Control Infrastructure.
The ANSPs need to develop their own intel, based on accumulated data, analyze the implications and initiate potentially required infrastructural modifications. Such a task-force is called Security Orchestration, Automation and Response (SOAR) team. ATSEP need to be part of the SOC, CERT and SOAR teams. Depending on the ANSPs strategy, the teams are fully part of the ATSEP department, or a mixed team of a separate cyber-security department and the ATSEP.
Every ATSEP will require an overview knowledge of the cybersecurity implications discussed. Team-members of SOC, CERT and SOAR will need qualification through specific cybersecurity specialization streams.
Trend #3: Vendor-consolidation
In Gartner’s research, 78% of CISOs responded they over 16 different solutions in their cybersecurity vendor portfolio, while 12% reported having 46 or more. Having numerous security vendors complicates security operations. There is increased interest in developing vendor consolidation strategies. While cutting costs appears to be a lead factor behind this trend, streamlining operations and reducing security risks are also believed to be more achievable. Therefore, large security vendors are likely to offer better-integrated products.
The market has understood that. There is an accelerated market consolidation process ongoing right now, with big security players like Thales, Entrust or Utimaco conducting refined M&A strategies to be able to offer full-line cybersecurity solutions.
On the other hand, vendors of data, surveillance and navigation solutions are adding cybersecurity components into their portfolio.
It will be difficult to defend one or the other solution. However, I perceive that the following basic decisions are important:
- The cyber-solution provider should be vendor-agnostic. The reason is simple: there is never only one manufacturer of radars, NAVAIDS, ATM or VCM system etc. in the structure of the ANSP. Also cybersecurity needs to embrace the whole infrastructure and should not be a patchwork of monolithic security solutions, allowing data to transit from one location to another. So the system provider should be able to provide public key infrastructure, ID, signing and authentication solutions for any application.
- An important lesson learnt from Total Quality Management in banking or the automotive world is that a multi-vendor strategy avoids vendor lock-ins. What happens if the one-only vendor cannot supply, has a technical problem or wants to re-negotiate. So our silver bullet would be to consolidate solutions but build on 2-3 cybersecurity vendors.
- The big cloud service providers like Microsoft, AWS or Google allow so called Bring-Your-Own Key solutions. Meaning that even data hosted in their infrastructures can be encrypted by an external cybersecurity provider. This allows ANSPs to design end-to-end secure architectures which also benefit from the advantages of cloud applications.
Trend #4: Identity-First Security
Fraud and cybercrime have increased during COVID-19 as businesses shifted to remote work. Identity-first security has been around before the pandemic and had been considered the gold standard, but not on the radar of organizations that had not started their digitalization transformations. But because of the unprecedented number of remote workers, it has become crucial for many organizations to address identity first security, not only for their remote workers but also for those in the office.
ATC is decentral by design. Digital identities are necessary to properly gate communication, they are the basis for authentication (multi-factor authentication) or digital signing (not only documents but also signed data messages). Europe has a powerful EU Regulation called eIDAS. It does not only include standards by the European Telecommunications Standards Institute (ETSI) but has the legal backing, meaning a message (even an XML message) has the same legal value as a handwritten signature. But it has a high legal level of assertion as it is technically non-repudiable as the digital proof is there.
ATSEP need to understand the roles of keys, certificates, certificate authorities and signing procedures. If systems or end-to-end procedures are modified, they shall always embrace digital identities and signatures (important note: not only digital signed documents, but also digitally signed messages like XML, as documented in the XADES standard based on eIDAS). Even legal entities can communicate through digital seals, which allows for automated non-repudiable messaging.
Trend #5: Managing machine identities becoming a critical security capability
Organizations are experiencing an increased number of multiple machine identities during their digital transformations. This has makes the need for managing machine identities a critical part of security strategies as the number of mobile devices, computers, and IoT/OT devices grow on their enterprise system. This explains the trend for improving the management of machine identities and certificates to enable more secure digital transformations.
Components and systems (like a radar or a NAVAIDS system) purchased need to have a key/certificate, otherwise they cannot be included. The principle is comparable to the digital ID of humans. Understanding this is a core competence of the ATSEP.
Trend #6: Remote Workspaces Becoming More a Norm for Some Industries
COVID-19 changed how people work and receive training. Gartner’s recent CIO survey shows that 64% of employees could work from home while 20% are actually doing so. In the past, remote workspaces were typically reserved for senior staff, executives, or salespersons. Looking to a post-pandemic future, there is a trend to shift more employees to remote workspaces permanently. This, of course, will require the need to improve cybersecurity policies, security tools, and infrastructure to mitigate the risks that come with the move to remote work.
ATCO and ATSEP will not be operating from home, but given the increased number of admin personnel and third party service providers, this means that the ATC network is getting even more decentralized. This fact impacts the security structure and needs to be incorperated into the security concept.
Trend #7: Breach & Attack Simulation for Increased Proactive vs. Reactive Response
A major component of ATSEP training has always been simulations of events that could happen. Employing breach and attack simulation (BAS) plays an important job in cybersecurity by validating an organisation’s security posture by testing its vulnerabilities to external threats. BAS efforts work to immediately identify deficiencies that interfere with the efficacy of security controls and help improve security assessments in near real-time.
SkyRadar's training environment for ATSEP does Breach & Attack simulation in a pedagogically designed and secure sandbox, including important ATSEP components like radars, RDPS, databases and communication. It is modular and can be included in a full Radar & Tower simulator.
Trend #8: Emergence of Privacy Enhancing Computation Techniques
In the past, the focus on protecting data has been focused on when it is at rest or in motion. Now, privacy-enhancing computation (PEC) techniques that protect data while it is in use are emerging. This enables secure processing, cross-border transfers, sharing, and analytics even when the environment's integrity is not necessarily secure. The move toward PEC will enable new forms of computing and sharing information while reducing risks of data breaches.
SkyRadar's cybersecurity training solutions for ATSEP
SkyRadar's modular cyber-security training infrastructure includes
- basic setting
- training radars,
- ADS-B receivers
- Flight Data Processing Systems
- extension: AI training systems
- full fledged Radar & Tower Simulator infrastructure: an operational ATM-system with Voice Communication System and simulated data inputs (operating as Tower Simulator and Radar Simulator)
The training system can be compromised by a cyber attack simulator. The simulator creates threat awareness and teaches threat detection, prevention and post-attack recovery around the ATSEP's working environment.

The objective of these practical exercises is to help to gain the following competences:
- Understand the nature and impact of cybersecurity threats and being able to judge system threats and vulnerabilities
- Learn to analyze latent threat-potential through security weaknesses in existing or new systems in a structured way and be able to close loopholes
- Learn to detect attacks and handle them with the objective to reach rapid system recovery and most limited damage
- Learn how to collect data and improve the ATC security infrastructure in a sustainable way.
The training system includes scenarios like:
- attack scenarios: sniffer attacks, insider threat, trojan horse, identity spoofing, upstream attacks, etc.
- defense scenarios: firewall, SSL, 2 factor authentication, code signing, electronic IDs etc.
Next Steps
Talk to us for your requirements on the Cyber Security Training Infrastructure. We can adapt the infrastructure on your skill requirements and if required, supply it integrated in a complete Radar & Tower Simulator, based on an operational ATM system. Or we simply connect your academy to our training infrastructure-as-a-service.
Our trainers can provide intensive train-the-trainer seminars at your location in various languages.
We are also keen to motivate ATSEP training academies to participate in requirement elicitation calls (to make sure that all needs are met), to sign up for online testing of our ATSEP B&AS and to discuss a potential curricula (which we would like to share freely with interested academies).

About the Author
 The author, Dr. Ulrich Scholten is cofounder of SkyRadar. He has been working on internet platforms since the early 2000s. Ulrich holds a PhD in information technology. He is author / editor of articles on cybersecurity with more than 30.000 monthly readers. His research is regularly published in highly rated journals and conference papers.
The author, Dr. Ulrich Scholten is cofounder of SkyRadar. He has been working on internet platforms since the early 2000s. Ulrich holds a PhD in information technology. He is author / editor of articles on cybersecurity with more than 30.000 monthly readers. His research is regularly published in highly rated journals and conference papers.
References
- Gartner Top Security and Risk Trends for 2021 (April 2021)
- Read more about Cybersecurity for ATSEP and AVSEC (2019-today), by Dawn Turner, Martin Rupp, Peter Smirnoff, Ulrich Scholten and Dennis Vasilev.