New ATM system generations will be more open and flexible, making them a target for cyber attacks and terrorism. This article discusses solutions for ATSEP basic and on-the-job education on cyber-security.
The risk of cyber-attacks in ATM
For years, Air Traffic Management rooted its robustness and reliability on closed, inflexible autonomous surveillance islands. The new generation of ATM will be defined by an interconnection of entities monitoring, exchanging, aggregating, enhancing and double checking surveillance data, flight data, weather, airport information and so on. Dynamic routing and integrated areas like the Single European Sky turn ATM into an agile, decentral closed-loop control system embracing systems of many vendors.
 This interconnection holds a huge potential for saving resources, efficiency gains as well as time and cost savings. But on the other hand it also opens flanks for malicious and sometimes accidental acts of data privacy and security breaches. In air traffic, this can have devastating effects on the life of passengers, crew and people on the ground.
This interconnection holds a huge potential for saving resources, efficiency gains as well as time and cost savings. But on the other hand it also opens flanks for malicious and sometimes accidental acts of data privacy and security breaches. In air traffic, this can have devastating effects on the life of passengers, crew and people on the ground.
In the past, ATCOs and ATSEP were trained to apply Electronic Counter Counter Measures on maliciously jammed or perturbed primary surveillance signals. Today, vigilance and counter strategies are needed for cyber attacks on the totality of surveillance and navigation systems, datalinks, radio and communication networks.
For the ATSEP, the utmost goal is to keep the ATM systems uncompromised and operative. In case of system degradation, escalation routines and skilled personnel shall limit the downtimes to a minimum.
ATSEP: the need for basic and on-the-job education
Costas Christoforou, the European director of International Federation of IFATSEA, emphasized in his ATM-cyber security presentation on Feb. 25, 2021 the need for cyber-security related staff and user education. This comprises
- basic and on-the-job training on cyber attacks and cyber terrorism
- education on new ANSP processes which take cyber security into account
- familiarization with Artificial Intelligence and Human Machine Interdependencies.
A cybersecurity reference architecture

The ATSEP needs to be skilled on cybersecurity architectures within ATM systems. Skilled means they need to be able to
- understand the architecture,
- discover and localize attacks or successful intrusion
- fix a depreciated or compromised system within the shortest possible downtime, following ANSP processes.
Understand the Architecture
The ATSEP needs to be familiar with typical components in a cyber secure infrastructure including firewalls, multifactor authentication, signed code, qualified digital signatures and seals. An important role play public key infrastructures to encrypt data at rest and in transit at all times, where the keys are accommodated in military-grade hardware security modules, managed by key life-cycle management systems.
Important components will be identifiable as attested devices with specific qualified electronic identities. Users and systems received access based on (qualified) electronic identities, managed and supervised by trust service authorities.
Discover and allocate attacks or successful intrusion
Intelligent AI-based analytics platforms and expert system support the discovery and localization of data breaches or malicious intrusions into systems.
The ATSEP shall understand the concepts of Artificial Intelligence, and the use, configuration and service of such systems.
Guided by analytics platforms, ATSEP should be able to discover vulnerabilities and terminate breaches within shortest response time. Depreciated systems need to be brought into a safe state in the shortest amount of time.
SkyRadar's cybersecurity training solutions for ATSEP
SkyRadar's modular training infrastructure includes
- training radars, ADS-B receivers and Flight Data Processing Systems
- AI training systems
- an operational ATM-system with Voice Communication System and simulated data inputs (operating as Tower Simulator and Radar Simulator)
The training system can be compromised by a cyber attack simulator. The simulator creates threat awareness and teaches threat detection, prevention and post-attack recovery around the ATSEP's working environment.

The objective of these practical exercises is to help to gain the following competences:
- Understand the nature and impact of cybersecurity threats and being able to judge system threats and vulnerabilities
- Learn to analyze latent threat-potential through security weaknesses in existing or new systems in a structured way and be able to close loopholes
- Learn to detect attacks and handle them with the objective to reach rapid system recovery and most limited damage
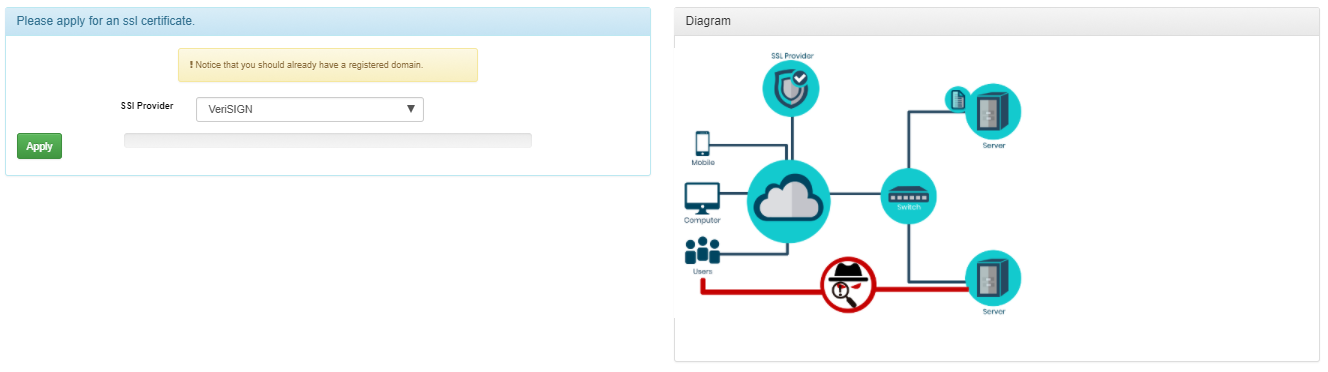
The trainer includes
- attack scenarios: sniffer attacks, insider threat, trojan horse, identity spoofing, upstream attacks, etc.
- defence scenarios: firewall, SSL, 2 factor authentication, code signing, electronic IDs etc.
Contact us to discuss your project!

The author, Dr. Ulrich Scholten is cofounder of SkyRadar. He has been working on internet platforms since the early 2000s. Ulrich holds a PhD in information technology. He is author / editor of articles on cybersecurity with more than 30.000 monthly readers. His research is regularly published in highly rated journals and conference papers.




