This articles describes how to tailor threat intelligence for information systems requires a dual approach. CSIRTs must prioritize internal data collection while keeping a watchful eye on external sources. The article shows how automation through the right tools augments insights, emphasizing the critical role of tool selection for effective attack mitigation.
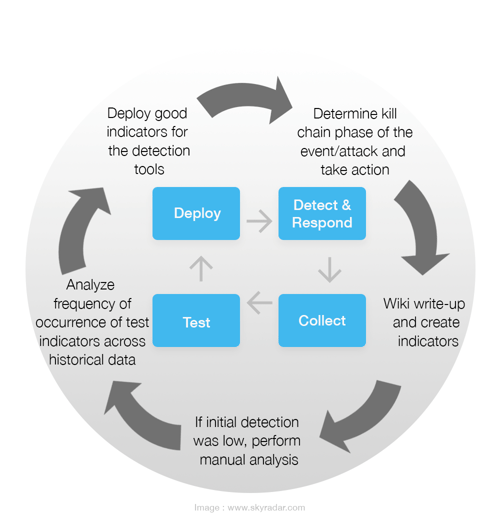
In our previous article The Incident Detection & Response Process, we introduced an agile iterative CSIRT process on how to set up indicators for detection, analysis, and responding to incidents:
If you want to uncover and disrupt threats before they impact your business, you need to understand what poses a real risk as quickly as possible. However, threats or risks can only be seen or understood if you have visibility into each of the risks.
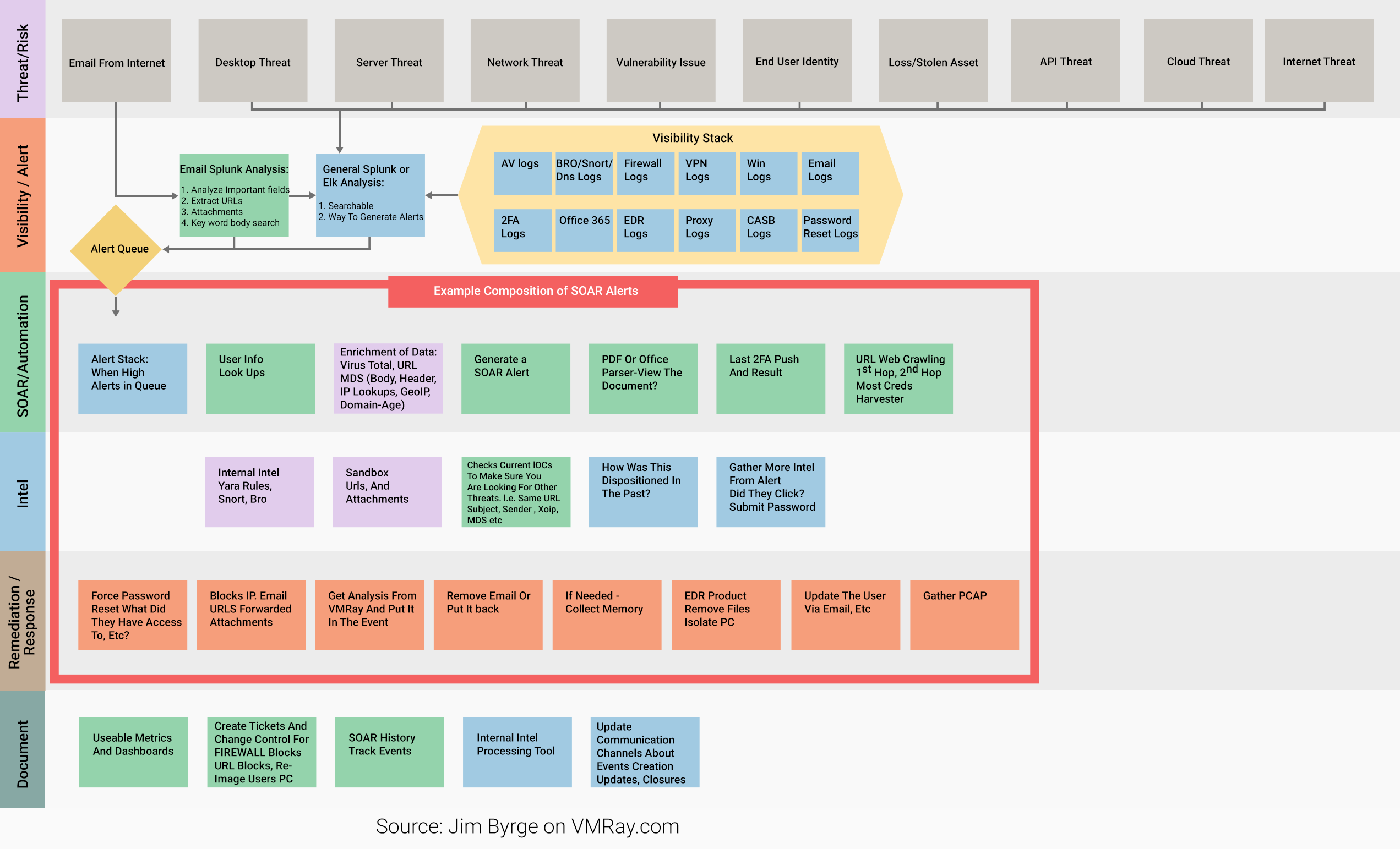
The experts suggested standard workflow - how it works
The following workflow is based on an ongoing collaboration of both internal and external intel following analysis of frequency of test indicators across historical data, the end aim being - understanding the problem and putting defensive strategies in place;
The Workflow - Swimlanes
- Threat/ Risk - Proactivity is the key difference between threat hunting and other security activities such as protective monitoring- become driven by curiosity. Detail the threats/ risks identified
- Visibility / Alert - Visibility is then required into each of the risks. This is achieved by gathering as much information as possible visibility wise- by talking to IT architects, business leaders etc and understanding exactly what is important - what 2FA is in place, firewalls, logs, EDR, emails logs etc
- SOAR/ Automation - Next, find ways to create automation and alerts. This can be achieved by constantly enriching data, adding screenshots and so on
- Intel - when alerts occur, intel will need to be available to support the incident response team - cyber threat intelligence & relevant data from across the estate - increase collection coverage across the estate into a centralized repository & constantly inform and enrich to share knowledge and lessons learnt
- Remediation/ Response - get to a stage where memory/ intel can be gathered automatically to create a layer for analysis. Do whatever is best for leadership and reward end users for reporting. Team collaboration is key.
Important Terms of the CSIRT process
Bro Logs is a network security monitor that provides enriched network visibility. During the course of its normal operation, Bro produces a large volume of log files. This series of exercises examines the Bro log output format and logs some extremely useful utilities that can be used to extract data from and/or process this information. This data is then used for incident response and cyber threat hunting.
A Cloud access security broker (CASB) is cloud-hosted software or on-premises software or hardware that acts as an intermediary between users and cloud service providers. The ability of a CASB to address gaps in security extends across software-as-a-service (SaaS), platform-as-a-service (PaaS), and infrastructure-as-a-service (IaaS) environments. In addition to providing visibility, a CASB also allows organizations to extend the reach of their security policies from their existing on-premises infrastructure to the cloud and create new policies for cloud-specific context.
CASB serves as a ‘policy enforcement center’- consolidating multiple types of security policy enforcement and applying them to everything your business utilizes in the cloud, regardless of what sort of device is attempting to access it, including unmanaged smartphones, IoT devices, or personal laptops.
Credential harvesting takes many forms, of which “classic” email phishing armed with links to bogus websites or malicious attachments is just one. Any or all of social engineering techniques, digital scamming and malware may be used to steal credentials.
Indicators of Compromise (IOCs) serve as forensic evidence of potential intrusions on a host system or network. These artifacts enable information security (InfoSec) professionals and system administrators to detect intrusion attempts or other malicious activities.
The cyber kill chain is a series of steps adopted from the military, which uses this term related to the structure of an attack. It consists of identifying a target, dispatch, decision, order, and finally, destruction of the target.
Snort is a free open-source network intrusion detection system (IDS) and intrusion prevention system (IPS), capable of performing real-time traffic analysis and packet logging on IP networks .
SPLUNK is a software platform to search, analyze and visualize the machine-generated, real-time data gathered from the websites, applications, sensors, devices etc. which make up an IT infrastructure and business. Splunk uses the data for identifying data patterns, providing metrics, diagnosing problems and providing intelligence for business operations. It is a horizontal technology used for application management, security and compliance, as well as business and web analytics.
Statistics on using Apple, DNS query and response details (also known as a DNS request) is a demand for information sent from a user’s computer (DNS client) to a DNS server. This request is usually sent to ask for the IP address associated with a domain name, connection logs, ID’s, Duration, http logs and FTP logs.
URL Master Data Services (MDS) provide information about Body, Header, IP Lookups, GeoIP, Domain-Age
URL Web Crawler is a type of bot that is typically operated by search engines. It can also help webmasters to find broken hyperlinks and is therefore used for security investigations , for example, analyzing links that appear to be manipulated with the intent to mislead users about their destination and purpose.
VirusTotal aggregates many antivirus products and online scan engines to check for viruses that the user’s own antivirus may have missed, or to verify against any false information.
YARA rules are used to classify and identify malware samples by creating descriptions of malware families based on textual or binary patterns. It was developed with the idea to describe patterns that identify particular strains or entire families of malware.
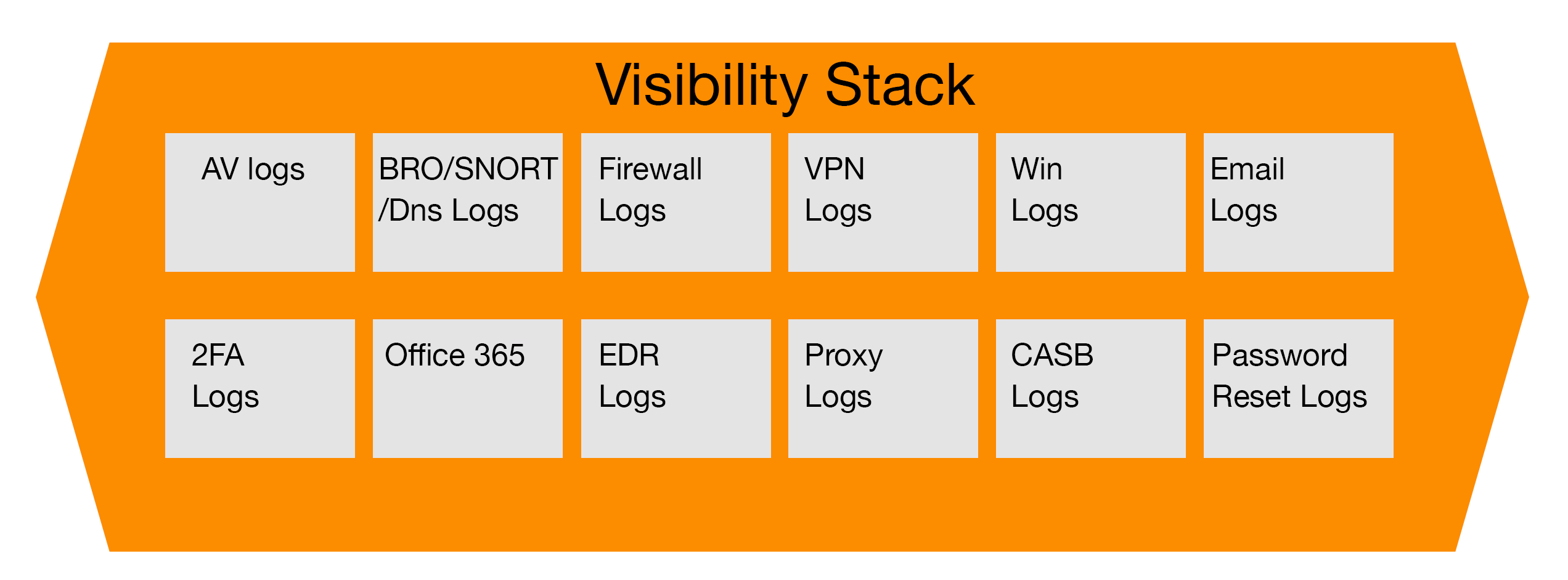
The Visibility Stack - understanding what’s important
A key part of the CSIRT process is the Visibility Stack;
After identifying the Threat/ risk areas that are key to your business (see first swimlane in the workflow), add the key areas for visibility requirements that will make-up the visibility stack. This can be achieved by talking to key areas such as IT architecture and business leaders in order to establish what is key to the business and what is the intention of these areas- what they already have in place or planned, what AV and multi-factor is used, Office 365 and firewall logs, what EDR is in already place and what’s happening on execution and imported information. These are all good examples. All these pieces of information can be applied to the Visibility Stack- all information needs to be searchable to the CSIRT team as well as ways to generate alerts on some of the key risks that are being detected.
The analysis of emails is an area of high importance and therefore, in this instance, we have intentionally used this as a prime example:
- Go beyond ‘header’ information. In header information there is no BCC filter, no undisclosed recipients. This information is normally contained within the envelope.
- Break the envelope into sections. Send the header into Splunk as well as the URLs (URLs - can be sent from various addresses, message id’s)
- Header, body, attachments need to be investigated
- Attachments- identify attachment names, macros, URL etc
- Separate these risks out and apply them to the CSIRT process (placing them to their own searching lane)
- Swimlane 3 (will then apply ‘SOAR/ Automation). Reduce alert fatigue as much as possible- some alerts would be higher up in the alert queue and pushed to a mailbox. Figure out what is high priority for the company
- User info look-ups. You need to understand who would be receiving the email- individual, what department/ business until they are in, email address, geographic area, manager. Is the email relevant to the individual's business area?
- Keep building until you have a complete Visibility Stack process and constantly enrich your data.
Read more in our detailed expert articles, which take a hands-on approach through each element of the security stack.
Workflows + Mitigation Tools = successful treatment of attacks
A key takeaway from this article is - to create threat intelligence customized to information systems, CSIRTs need to collect data internally. External sources should be monitored for threat data related to any components or tools used. Tools can be utilized, which can automatically return relevant information that can provide additional context for analyses. As a result, it is important to select appropriate tools that will support the successful treatment of attacks.