When it comes to incident response, the quicker a business deals with the threat, the better. It’s not just about being able to respond in a timely manner, it’s also about having the right persons and plan in place to deal with the event effectively.
In the rapidly changing landscape of air traffic control and aviation security, the swift and effective response to incidents is vital. As the interconnected infrastructure faces an array of digital threats, the establishment of a robust Incident Response Team takes center stage in safeguarding the integrity of air traffic control systems.
This article embarks on a journey to explore the intricacies of building an efficient Incident Response Team, with a particular focus on the pivotal role played by the team leader in orchestrating this vital aspect of security.
How to Build An Effective Incident Response Team
Incident response teams are often divided into segmented functions such as patching, scanning, coordinating and communicating with the key parties involved in responding to an incident. They often have to work on an individual basis, in close cooperation with other teams, and under time constraints. Hence, teamwork is of the utmost importance - failure due to lack of collaboration could have disastrous consequences.
Incident response within an organization is paramount. Probably the most important role that security practitioners will ever have to do. Planning, mapping, analysis, communication, external persons, legalities, costs - and this is not an exhaustive list. Also, companies have different requirements depending on factors such as regulatory requirements and the industry in which they operate. This means that no two incident response teams will ever be the same.
Because of this, some things cannot be fully automated, and incident response is one of them. No two incidents are alike. Although process maps can and need to be created, escalation and communication paths described, prepared and aligned. That’s why having an incident response team equipped and ready to act - before an incident happens - should be at the heart of the business.
However, where does a business start? How can the team be armed? How do they stay focussed? And where does the business start when assembling and organizing a team?
“Incident Response needs people, because successful Incident Response requires thinking.” — Bruce Schneier, Schneier on Security
A company may not always be able to justify a permanent position for a niche or highly specialized skill set, and the team may need to have different layers of knowledge. As a result, a blend or mix in the following tiers are likely;
- A standing incident response team allocated within the security operations center (SOC)
- Formed of key players within the IT and security function of a small to medium sized organization
- An external team that reacts when called upon
- A team of employees and/or third-party members
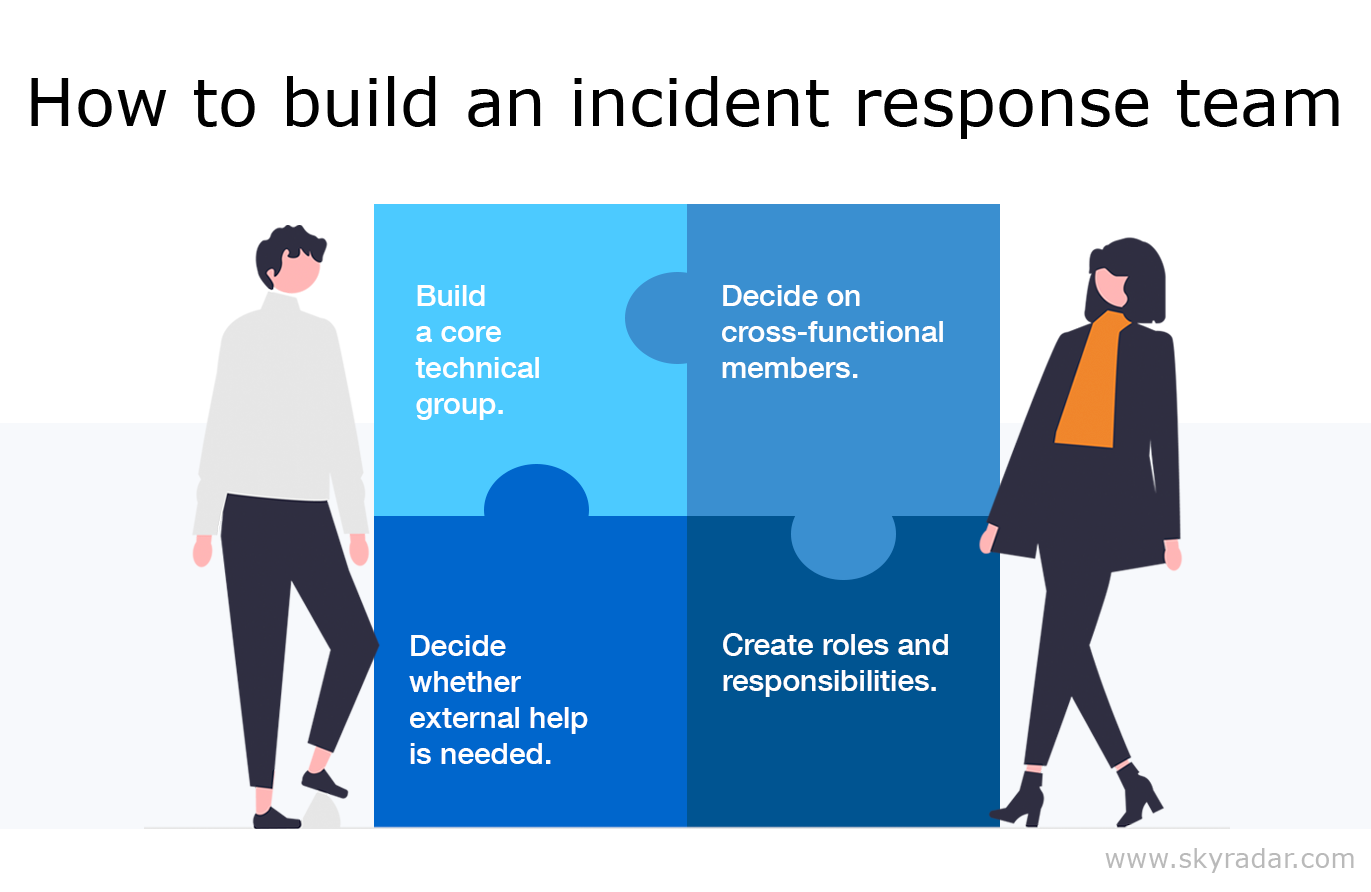
Source: How to build an incident response team for your organization
The Incident Response team is therefore often set up as a separate group outside of the IT Help Desk. Their focus should not be diverted away from disarming attacks, and they should be evaluated on this basis.
A High-level CSIRT
“If you’re not doing scans and penetration tests, then just know that someone else is. And they don’t work for you” - George Grachis, Senior Consultant, Maxis360
Make assertions, not assumptions. Imagine from the attackers perspective
In a webinar from, VMRay and Valvoline; Jim Byrge explains how he built their cybersecurity team at Valvoline and how a ‘you should assume that you are compromised every day’ mindset is at the heart of their vision
As companies seek to stay ahead of the latest cyber threats and rapidly respond to any potential attacks, a proactive mindset is key. Therefore, assuming that you are compromised every day and that adversaries are already in the system is a critical component to incorporate into the foundation of any incident response team.
The team should not be the only staff responsible for addressing security threats.
All business representatives and employees must fully understand and advocate for the incident response plan to minimize exposure to vulnerabilities and to ensure that emergency procedures run smoothly. However, keep in mind that structures and actual responsibilities vary from one organization to the other and a high level structure could look something like this;
- CSIRT Team Leader - The CSIRT Team Leader coordinates the incident response plan and puts together a team, while the manager oversees and prioritizes actions during the detection, analysis, and containment of an incident. In addition, this position is responsible for coordinating and relaying information to senior leadership and managing stakeholder expectations.
Indeed, the team leader needs to be able to talk to the senior leadership and relate the value in the program.
Security is something that if you do it well, people don’t see. Keep it in front of the leaders. Give reports on events, processes coming out of the program and how you are improving the security of the company. The role requires a mix of technical understanding and managerial skills.
- CSIRT Members - The CSIRT Members Gather and analyze technical evidence, determine the cause of the attack, and direct other analysts and IT components to implement system and service recovery. Managerial and leadership skills are a requirement for this position.
Responsibilities also include monitoring potential incidents and escalating them whenever a breach or security issue arises. The frontline workers of the team are tasked with making solid recommendations about new threats and potential security issues.
Ed Moyle explains in this article ‘Cert vs. CSIRT Vs. SOC: What’s the difference?’ that the typical workflow of a cross-functional incident response team would be:
Preparation > Detection & Analysis > Containment, eradication & recovery > Post-incident activity
Corporate and Executive Awareness
Finally, after setting up a team and having developed an incident response plan, this then needs to be communicated across the company. The CEO and executive team will need to review and approve the project charter and draft plan. Once approval is received, let the company know about the Incident Response team and its charter, particularly as to how you will be communicating to necessary parties in the event of any incident.
The team and processes may well change as those within learn from experience - constantly changing, adapting and refining processes and methods of communication.
There will be security incidents that are out of the incident response team’s control. How they are handled based upon the build of the team dedicated to dealing with these incidents will ultimately depend on the manager of the team.
Air Traffic Control Infrastructure
In conclusion, as ATC becomes increasingly interconnected and automated, the formation of a vigilant and capable Incident Response Team stands as a crucial pillar in the defense of resilient air traffic control systems. With dedicated leadership and a commitment to proactive readiness, these teams have a central role, working diligently behind the scenes to ensure the safety and security of our skies. The ever-evolving nature of cyber threats demands ongoing adaptation and refinement, reminding us that the protection of our airspace is an ongoing journey, one where vigilance and preparedness remain our steadfast companions.
Parts of this article were inspired through a webinar by Jim Byrge, published on VMRAY.com .




