Typically, when sophisticated drones or warplanes approach in enemy territory, they cover their real location through a DRFM jammer. They are more intelligent and difficult to dismantle than the classical noise jamming.
Three Categories of Deception Jamming
There are three deception categories which are applied either individually or together.
- range deception
- angle deception
- speed deception
Applying all three together, the intruding aircraft or drone can create complex and pretty realistic but completely fake scenarios. This challenges radars and radar operators. We therefore provide in our Electronic Warfare Product Series algorithms to clean the radar image and to bring the real targets back to visibility (disturbance filtering and analysis I, disturbance filtering and analysis II)
In Focus: Range Deception
In this article we will look at range deception.
It works as follows:
Range deception is created through DRFM jammers. Digital Radio Frequency Memory (DRFM) jammers digitally capture and retransmit RF signals. In the case of range deception, they delay or advance the "reflected" signal. The surveillance radar consequently gets a wrong impression of the target position. But how does the real drone or aircraft (the one that carries the DRFM jammer) disappear? The jammers make use of the radar lock-on principle.
Radar Lock-on and Range Gate Pull Off
First you need to know the following: The radar creates a range gate around the presumed targets and adapts the threshold around the gate that all clutter disappears below the clutter threshold level. Deception jammers exploit this.
The deception jamming works in the following way: .
First it creates a cover pulse over the real target's reflection. It is much higher than the reflection of the real target. The surveillance radar reduces the gain in this range gate with electronic circuits at the radar receiver, in order to control the amplitude of the covered pulse. We call this Automatic Gain Control (AGC). The consequence of this cheat: the real target disappears below clutter level.
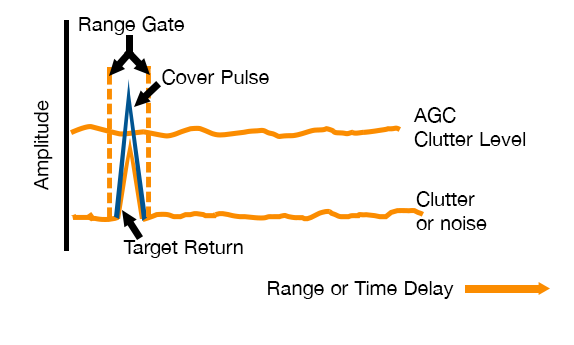
Image source: Electronic Warfare Fundamentals
In the second step, the reflection is delayed through the DRFM jammer and dragged away. We call this: Range Gate Pull-Off. The DRFM accomplished the pull-off through a change in time delay of the reflected signal.
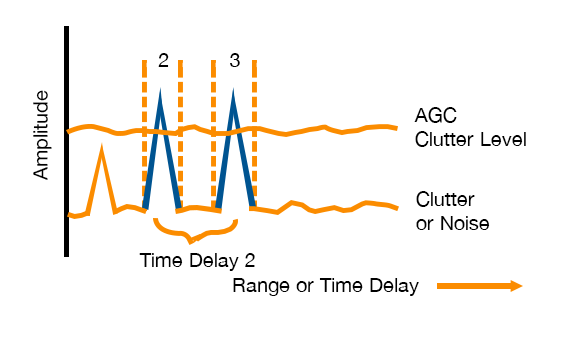
Image source: Electronic Warfare Fundamentals
In pure range jamming, the fake signal will stay on the radial axis of the radar. When mixing with angle and speed deception, the fake reflection can even move outside the radial axis.
The weak point of such a scenario is the first moment, when the radar initially detects the target. In the forthcoming articles you will learn how we can use this initial weakness to detect the deception attack.
Implementation with SkySim and FreeScopes
In the following video we compare the real and the fake signal, generated through range deception. We created the deception through SkySim. Technically we can also do it with our jammer attacking our NextGen Radar. The visualization but also the application of detection algorithms is done in FreeScopes.
In the second video of this series you will see the typical Range Gate Pull-Off Process. Don't miss it.
There is much more in SkySim
Follow our blogs and videos on SkySim to learn more about the simulator, range deception, angle deception, speed deception, radar lock on and major state of the art defense algorithms against malicious attacks.
Such defense is not only useful in a military context but also in a civil aviation setting. Increasingly speed radar jammers by trucks and cars disturb airport infrastructure.
Let's talk
Stay tuned to be always the first to learn about new use cases and training solutions in radar qualification (real radars or simulators) for ATSEP.
Or simply talk to us to discuss your training solution.




