Malicious actors regardless of motivation, whether financial or hacktivism, tend to look for the path of least resistance. In many data breaches, when forensic teams investigate the root cause, they end up tracing it back to email as the initial vector of the breach, where it all began. The reason this turns out to be the most lucrative for all attackers is the fundamentals of human psychology.
Threat actors understand their targets and research them heavily prior to sending phishing emails, spear phishing emails as well as emails that are termed as Business email compromise. Many organizations of all sizes still struggle with getting the filters correct and lack sandboxing capabilities to analyze emails before they get to the end users.
Initial Phase of Intrusion - Recon
As this is still a huge struggle for organizations of all sizes, let us take a business email compromise as one we will examine and investigate for this phase. In this example, we have a large energy company that depends on various shipping companies to transport their oil and raw materials around the world to various refineries. The energy company seems to have robust end point and email filters on their network, the threat actors learn this during their reconnaissance phase. The hackers really want to get money from the energy company but know they will need to find a supplier within their supply chain that has weaker security controls. In order to pull this off, the threat actors will need to set up infrastructure to make it believable. This will be explored further in our analysis of other parts of the security stack, but the threat actors create a spoofed shipping company ABC exports which is close to ADC exports, the legitimate shipper.
Secondary Phase – Compromise of 3rd Party
The legitimate shipping company has now been compromised by the attacker via a phishing email and lucky for the attackers, this company does not have multi-factor authentication in place on their user accounts. Now that the attackers gained a foothold in the secondary victim environment, they will now remain dormant but first set up forwarding of target emails to their new domain they set up so they can monitor it. Once they see a transaction about to take place between the two unsuspecting companies, they will intercept the message and spoof the shipping company in many cases, and re-type it stating they need the energy company to update the payment details for the account, so the money is routed to the attackers instead of the legitimate shipping company.
Attempted Fraud Phase
Many emails such as this are not stopped by email gateways, however, it is standard practice across industries to tag emails inbound as “external sender” with a banner at the top of the email to try and alert the recipient. However, this is not always caught or paid attention to due to how desensitized many have become due to the routine of business, engaging with parties outside the business as part of normal practice. In this scenario, our energy company, which was the ultimate target, did not catch the email that was sent requesting payment information to be changed. The incident response team is alerted* to the fact that someone in accounts payable, initiated the change in banking details without contacting the supplier to ensure it was indeed a legitimate change request.
Incident Response Team Follow Up Actions
While the breach did occur, there was no actual breach of the energy company’s actual systems. So, how do teams investigate what happened? There are several components to this, but the primary steps involve the original email and the email gateway security solution at the target company.
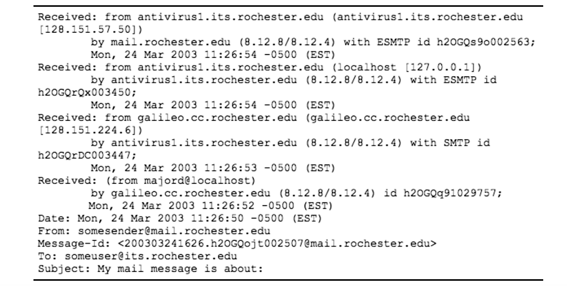 Fig 1. Sample email header from Rochester.edu
Fig 1. Sample email header from Rochester.edu
There are plenty of tools to aid with the investigation of raw email headers such as www.mxtoolbox.com which will parse the headers nicely to show the true origin of the email. This is very important to determine if the supplier was truly compromised or if they were spoofed but the emails were not caught. If the domain was spoofed, the team should investigate with tools like domaintools.com when it was created and hopefully by who. Aside from the original email header which shows the true path the email took to get to your organization, reviewing the transport rules it passed through in your email gateway is very important. If the domain was spoofed, then you should investigate whether anyone else at the company received it and if so, delete them from their inboxes and block the spoofed sender, then the team would need to alert the supplier of the breach on their side as well and request they implement MFA if it is not already in place and ensure that the true person that was spoofed is not compromised in other ways such as malware on their work machines.
In the next article, "Investigations Using Proxy Logs", we will discuss the next component of the security stack which is the web gateways or firewalls.
The IR team could be alerted in a number of ways, such as if a user reported it to the company security mailbox or through routine monitoring that incident response teams perform as a normal part of their practice. When security teams monitor a company network, they monitor each layer together not separately.
Read the next article in this series, shedding light on proxy logs or read the complete security stack series.
References
- Infographic: University of Rochester - Interpreting Email Headers
- “Building your Cybersecurity Program” (2021), by Jim Byrge in cooperation with VMRAY.com