CASB solutions can help your business in addressing risk in cloud-based services, consistently enforce security policies and comply with regulations, even when these services reside beyond your perimeter and out of your direct control. The value stems from the ability to identify high-risk applications, users, and other key risk factors across cloud platforms - a potential blind spot for many businesses.
Let’s Define CASB
With the various acronyms used in cyber security and networking, let us take a moment to define what a CASB truly is. CASB stands for Cloud Access Security Broker, its primary function is to act as a secure gateway between cloud operations and how users interact with the data. While various vendors have similar functionality, the core operations allow for visibility, compliance, data security and threat protection.
As organizations across verticals work to reduce costs of computing and operating on premise and provide a more flexible work environment due to the ongoing pandemic, the criticality of having a proper CASB in place is rising in importance for security teams to consider. There are two primary methods in which security teams interact with the data available from these tools, which are either having the data fed into a SIEM or log manager such as Splunk, or teams will dedicate time everyday to log into the console directly to review alerts and activity observed.
With these solutions in place, incident response teams can take advantage of the wealth of information it provides for threat hunting and investigations of ongoing incidents.
Investigations and Mitigations with Cloud Access Security Brokers
The following are some of the key benefits of implementing and managing a CASB:
- Discover Saas, IaaS and web use details, and quickly assess potential risk
- Secure your approved cloud services such as Office 365, Box and AWS
- Safely enable unauthorized, business-led cloud services instead of simply prohibiting them
- Govern cloud and web use for users who are on premises, mobile or remote
- Guard sensitive data with advanced DLP
While Cloud access security brokers do an excellent job at mitigating threats, enforcing security policies, and alerting on violations either in policy or malware events, there are threats that can and do make it past these solutions. As threats can spread across various cloud environments, incident response teams need solutions such as this to help them quickly identify the scope and breadth of the incident.
Having these solutions in place can also help identify which endpoint was involved with the breach if it originated from a user machine or server. With CASB in place, all activity is passed through these nodes and typically have a central management console which allows for quick identification and remediation of malware infections, user account compromises and gaps identified within cloud containers.
Considering Microsoft has established itself asa large player within the cloud space as well as their ecosystem which includes Defender for endpoints, and now they have implemented a security and compliance dashboard which allows teams to review alerts for users at risk, cloud applications at risk among other key data points of interest. Incident response teams can log into the Microsoft portal to review threats identified and, through playbooks and automation built in, can streamline, and expedite remediation of discovered issues.
For a direct example of what CASB’s such as Microsoft’s provides, see the following overview taken from Microsoft’s documentation:
Open alerts
Shows the number of open alerts, a graph of the alert status distribution, and recent alerts
- Discovered apps
Shows the number of discovered apps, a graph of the app risk distribution, and the top app categories by traffic. - Top users to investigate
Shows the number of users to investigate and the users with the highest investigation priority. - Conditional Access App Control
Shows the number of apps protected by Conditional Access App Control as well as the number of protected sessions and actions over the last 30 days. - App connectors status
Shows the number of API connected app instances and their status. - Files infected with malware
Shows the number of files infected with malware. - Privileged Office 365 OAuth apps
Shows the number of rarely used OAuth apps granted highly privileged permissions. - Azure security configuration
Shows the number and severity of Azure security configuration recommendations. - AWS security configuration
Shows the number and severity of AWS security configuration recommendations. - DLP alerts
Shows a graph of DLP alerts over the last 30 days.
Other platforms offer similar insights into your distributed cloud environment and incident response teams can gain immense value and insight with minimal effort with what comes out of the box from these vendors.
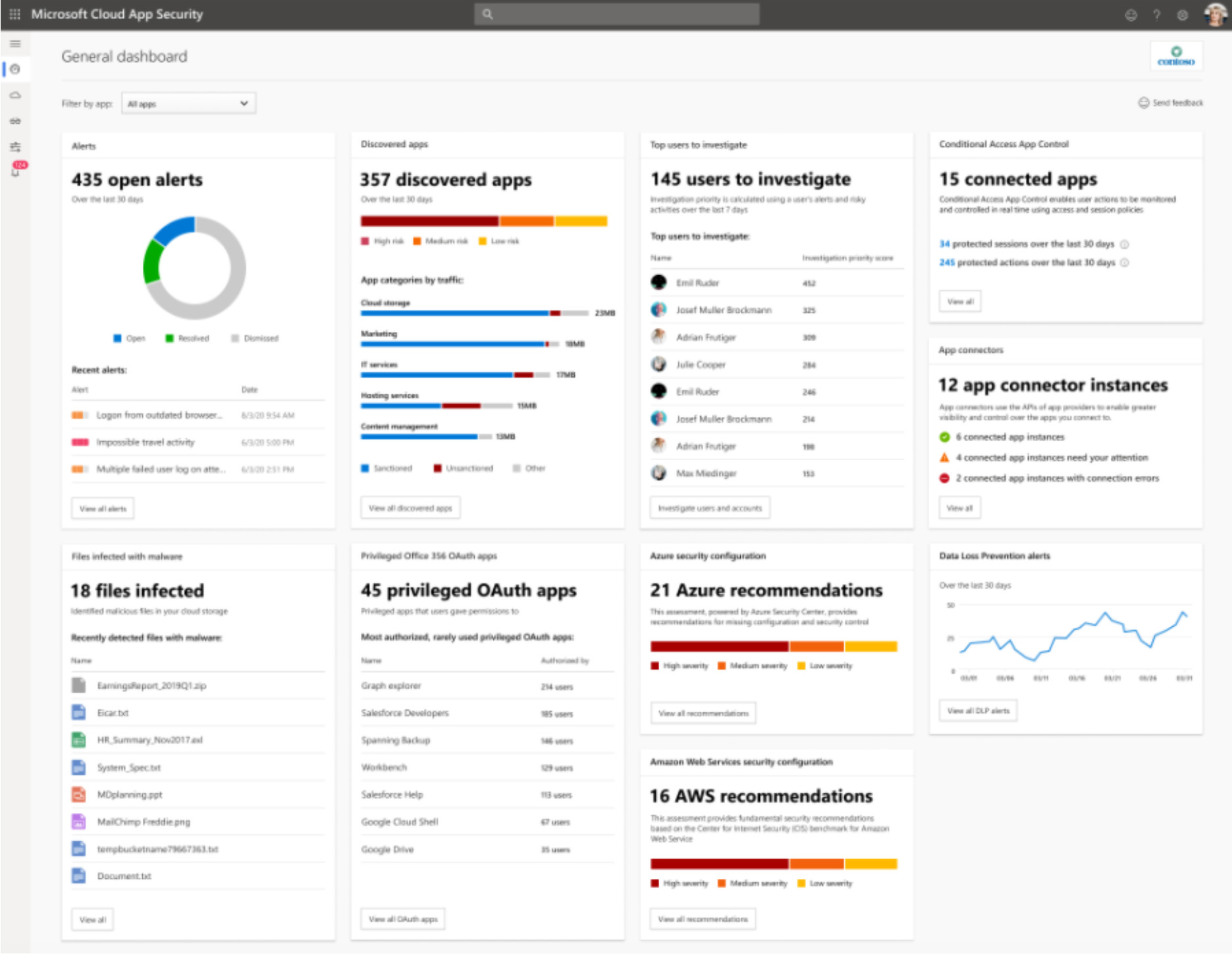 Source: (https://docs.microsoft.com/en-us/defender-cloud-apps/daily-activities-to-protect-your-cloud-environment)
Source: (https://docs.microsoft.com/en-us/defender-cloud-apps/daily-activities-to-protect-your-cloud-environment)