As part of our ongoing series regarding how each part of an organization’s security stack helps the incident response and forensic teams perform their analysis, we are going to now discuss Office 365 logs and the details it captures as teams interact with services held there.
The Move to the Cloud and Office 365
With the promises of the cloud for organizations of all verticals, especially those in the financial industry, a majority are making the time and investment to migrate their on-premise data centers to the cloud whether it is Azure, Office 365, Google, Amazon or the many others. With this move, it makes it more critical that those responsible for security and investigations understand what data is being migrated, how it is being stored and protected and ensure they advise their organizations they need to ensure proper logging levels are enabled and are being stored for at least a year or more for investigations. When it comes to various threats, whether insider centric or external hacking, preparation is key to be able to detect malicious activity and also to be able to respond in a timely manner to mitigate damage to the organization.
Investigating Insider Threats in Office 365
One of the threats organizations face, especially in today’s economy, is insider threats. As companies look to reduce staff and overhead, the risk of employees taking data leading up to their termination or lay off grows exponentially, especially if the corporate culture is not very pro-employee. In many cases I have investigated where an employee left due to layoffs, they had prepared for this by exporting data from data points within Office 365 which included OneDrive data files, client lists and contact information located in company SharePoint sites hosted within the Microsoft Cloud ecosystem, as well as other project sites and web-based email.
Leveraging Audit logs in Office 365
Many people are unaware that Microsoft captures extremely granular details on user activity within the Office 365 environment, which includes screen captures, log in/log offs, what is shared in Teams chats as well as changes to security groups, suspicious volume of data being downloaded, suspicious network access outside of normal behavior patterns for the user as well as USB usage. One item to note here, is that the level of logging available to your organization is entirely dependent on the licensing levels purchased. Most of the fundamental logging that can help your investigation can be done with the E5 Security Licensing, for a more comprehensive data set, a higher license will be required.
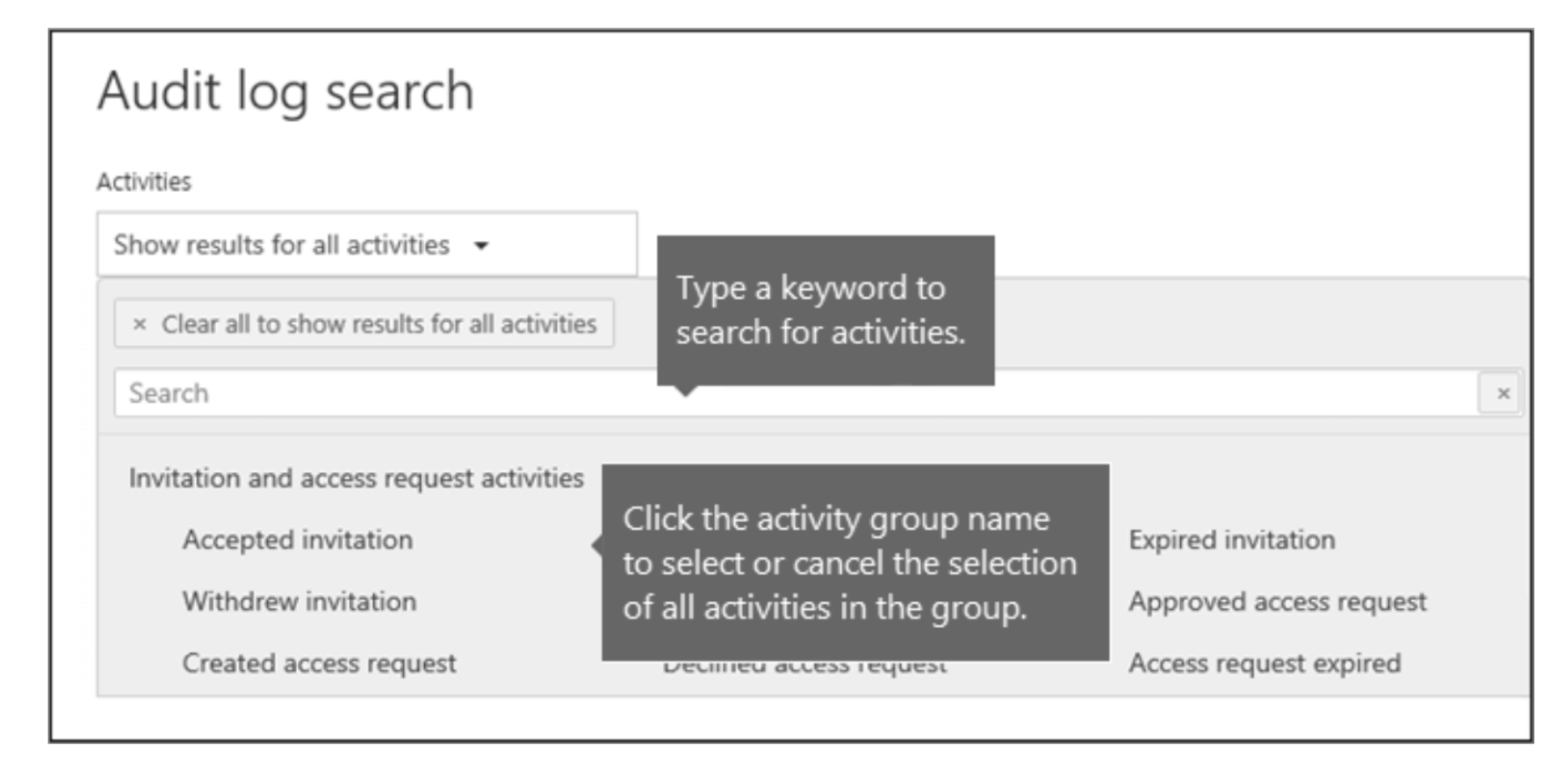
Fig 1 Audit log search menu sample (source: https://docs.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide)
Configuring the Search in Audit Log
As with any other tool that provides logs, you have to configure your searches within Microsoft Audit Log to drill down into what you are looking for. For the purpose of this article, we will focus on the most common methods data is exfiltrated from companies and financial institutions which includes, forwarding of emails to external accounts, downloading large volumes of data and files to a local machine and USB usage, other examples are screenshots which can be detected by Office 365 logs if enabled. Human Resources typically ask for these vectors to gauge if the employee is preparing for a move to another company or competitor. It is however important to comply with the relevant privacy regulation in your company’s area of jurisdiction. For an international player, jurisdiction might vary between the locations.
Executing the Search
To conduct the investigation, the key fields to search on include the username, the time range if the requestor wants a 30 day or longer history and the type of activity in question. Once you initiate the search and receive the results, you can schedule it to run every day if you need to monitor the user for a period of time throughout the investigation.
If any results are returned on the user activity, you will need to review it to ensure it makes sense and download the results to an excel document. Once the file is downloaded, the incident response team will need to carefully review it and parse the data to ensure it is readable by non-technical staff such as Human Resources or Legal. The potential outcomes from investigations like this could result in the termination or legal recourse against the accused, so it is imperative that the data pulled is accurate and the incident response teams can clearly articulate and display their findings.
In the next articles of this series, we will focus on other components of the security stack and how they interact to help incident response teams identify the full scope of an issue and how to remediate it.
References
- “Building your Cybersecurity Program” (2021), by Jim Byrge in cooperation with VMRAY.com