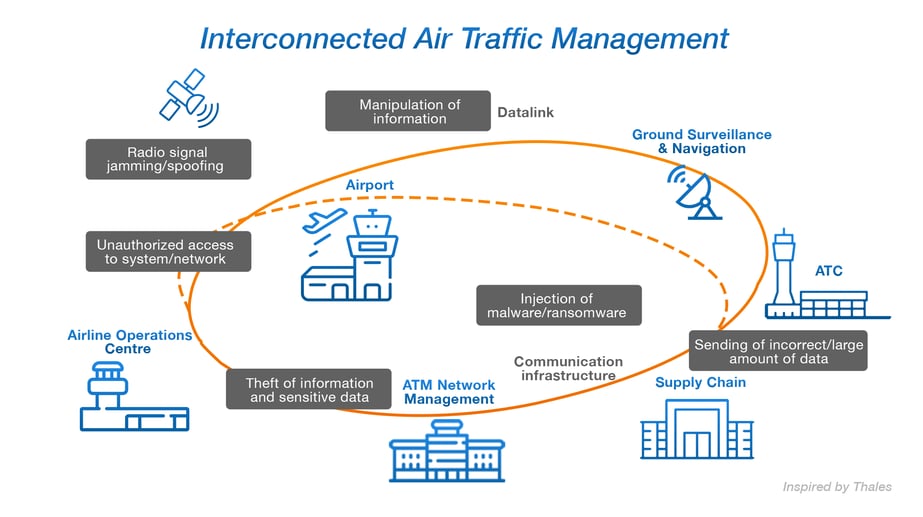
SkyRadar’s ATC Breach ,Attack & Defense Simulator has been developed to train ATSEP personnel on how to react to cyberattack in a targeted way, in escalation routines and with minimum down-times. It is part of the modular FreeScopes suite for ATCO and ATSEP training. We refer to it as the BA&D.
In this article, we dive quite deep into the world of breaches and attacks in air traffic control. The text includes many technical details and examples to give the technically proficient trainer, ATSEP curriculum responsible experts in the academies, but also the CISOs an insight into possible threats and SkyRadar’s response to professionally qualified ATSEP personnel. Those who are not yet familiar with cyber-defense should also take the time to read through the article. It will pay off.
The BA&D covers several complementary goals:
- Provide a general background in understanding cyberattacks and cyber-defense
- Demonstrate how attackers can concretely damage, fool, interrupt or even destroy an ATC infrastructure
- Demonstrate how cyber-defense works and what mechanisms are needed to inhibit the cyberattacks previously demonstrated in 2)
- Provide hints how to quickly react to an ongoing cyberattack
The BA&D is delivered as a set of docker components interacting together in a simulated ATC network. The ATSEP can be accessed via a mini-shell panel within FreeScopes, which provides all the tools needed to interact with it. Finally it is possible to visualize the effects of the attacks via - both - an ATSEP/ATCO view and an attacker’s view.
Overview of the attacks
The cyberattacks in the BA&D are of diverse nature and will have multiple effects on the (simulated) operations of the training ATC infrastructure. In general such cyberattacks are also referred to as ‘system penetration’.
Cyberattacks Goals Vs Cyberattacks techniques
It is important to distinguish between the cyberattack and its effects (or goals) . Disrupting the ATC operation is not an attack, it is the (possible) effect of a cyberattack. The same effect could be obtained by other ways which are not cyberattacks. There are various techniques and there are also, independently, various goals:
- Penetration of the system for “fun”, not monitoring or damaging anything (e.g., a Grey Hat operation)
- Spying out data (‘read-only’), in an untraceable way
- Capturing the data for blackmail or reselling these data to a darknet marketplace
- Ciphering the data, making the system inoperant and asking money (ransom) to have the system back to normality
- Destroying partly or totally the system for various reasons (war, retaliation,...)
- Using the system for personal goals
These are the goals of cyberattacks. Cyberattacks on the other hand are techniques which use flaws in implementations, designs or logic to make a program behave in a non-conform way.
Some of the Cyberattacks techniques
-
Flaws in communication protocols
A communication protocol defines how data is exchanged through a medium (copper cables, air…) including the language used by the machines for communication...
The terms “TCP/IP” or “HTTP” or “HTTPS” refer to such protocols.
The protocols are defined in several layers which are usually embedded inside each other (a bit like the Russian dolls, the Matriochkas) and defined by the OSI model.
|
Sigle |
Full Name |
Level |
|
I2C |
Inter-Integrated Circuit |
2 (data link layer) |
|
Token Ring |
Token Ring |
2 (data link layer) |
|
Ethernet |
Ethernet |
2 (data link layer) |
|
IP |
Internet Protocol |
3 (network layer) |
|
TCP |
Transfer Control Protocol |
4 (transport layer) |
|
HTTP |
HyperText Transfer Protocol |
7 (applicative layer) |
|
HTTPS |
HyperText Transfer Protocol Secure |
7 (applicative layer) |
An attack at the level of a protocol means that an attacker was able to find some default in the logical flow of the data to make the protocol behave incorrectly. This can potentially crash devices, inject remote code to a device or break some security, if this is an attack against a secure protocol.
Note that a protocol usually contains a lot of data flow control, synchronization, checksums etc… so that finding flaws in their logic is not easy. Nevertheless most of these protocols were not developed with the goal to protect them against malicious attackers but rather to prevent transmission errors. For example the messaging services such as POP or SMTP were not primarily developed to prevent massive inordinate use such as the SPAM (which is technically, a type of attack against a protocol)
Flaws in protocols can be very hard to solve and to patch.
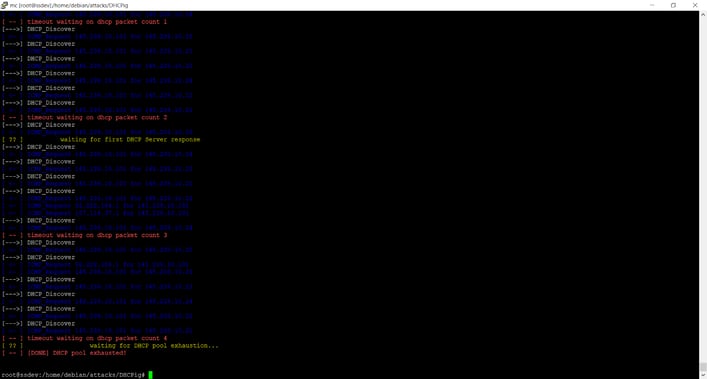
The BA&D includes a protocol attack against DHCP, which is, according to OSI classification, a level 7 - application - protocol.
DHCP stands for Dynamic Host Configuration Protocol. This is a protocol used by routers to allocate IP addresses to machines in a network. The BA&D will show how a simple tool using the DHCP protocol flaws - the DHCPig- can be used to create a complete denial-of-service in an improperly protected network.
Picture 1- DHCPIG in action
Picture 2- DHCPIG in action
-
Flaws in software
A software presents a certain amount of entry points for the users. They can be various. For example we can list the following entry points:
- Socket ports allowing communication with the software (server…)
- Libraries exposed by the software
- User interface (GUI, buttons etc …)
The program can be an implementation of a protocol. So the protocol itself is not to blame but a faulty programming is to blame.
For instance, in the case of the Eternal Blue attack (“exploit”) . This is not the SMB (server message block) protocol which is to blame but the programming of the protocol itself by Microsoft.
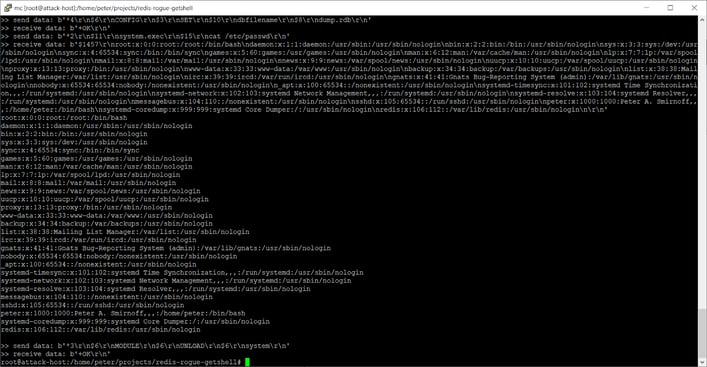
The BA&D proposes as an example of software attack, the Redis Rogue Server attack.
Picture 3- Redis protocol analysis
Picture 4- Redis Rogue server attack in action
REDIS is an in-memory data structure store, used as a database, cache, and message broker. It is not supposed to be used in the ‘outside world’ but only in well-protected networks. Nevertheless, the principle of the attack is that an intruder in a network can create a rogue server and attach it to an existing Redis server as part of a Redis cluster. At the end of the attack, the intruder has a remote shell into the machine!
Here this is the logic of the application which is attacked via an open port used for communication.
-
Bruteforce/cryptanalysis
Another type of attack is directly trying to break the security of systems, for example getting authenticated without the proper credentials. The simplest form of this attack is breaking a password, but this can also consist of breaking captcha or biometric identification
In such an attack, the cryptographic system is examined with the pursuit of finding weakness. The weakness could be a statistical weakness for example. The Shannon entropy is a simple, but efficient enough measure of the ‘complexity’ inherent to a password and especially a good measure of the quality of randomness.
A password with “weak entropy” is a password which has poor complexity and contains only a few letters or words from a dictionary.
“leo123”,”blastX”,”aabbcc1” are examples of such weak passwords.
An attacker usually will try to guess such a weak password by using a bruteforce attack or by combining a bruteforce attack and a dictionary attack.
The BA&D proposes such an attack , using a tool named kali. The tool is able to enter into private networks which are lacking adequate anti-brute force protection. Unfortunately, the vast majority of remote access is still using a plaintext password as a single way of authenticating a user without any second authentication factor.
-
Flaws in computer settings, OS & usage / using phishing and malwares
A less obvious type of attack uses a combination of bad settings, careless usage of the internet and OS flaws.
Typically this allows the propagation of viruses, especially troyans via channels that pretend to be legitimate (or even, much worse, who are legitimate)
In such an attack, a careless user will download & execute a binary software on his own machine, thinking it is legitimate and that it will fulfill a certain goal (game. software upgrade, music, tool…) . In reality the program is a malware and will behave maliciously. For example, allowing the attacker to access the machine via a remote shell.
The channel of distribution of the malware can be totally illegitimate ( a malicious website pretending to be a legitimate one , using phishing for instance ) or this can be a totally legitimate channel. Apple store or Google store for example since the verification process inherent to these channels doesn’t allow to block several type of malwares
The BA&D proposes the demonstration of a simple trojan based on netcat , which will open the local shell to a remote attacker.
Summary: attacks vs goals in the BA&D
In the BA&D , for the 4 basic types of attacks, the matrix Attacks vs Goals will be as follows:
|
Attacks\\Goals |
Denial-of-service |
penetration/intrusion |
Data modification/sabotage |
|
DHCPPig |
X |
|
|
|
Kali-bruteforce |
|
X |
|
|
Redis |
X |
X |
X |
|
Netcat |
|
X |
|
BA&D components & virtual network topology
Docker components
Few words about docker
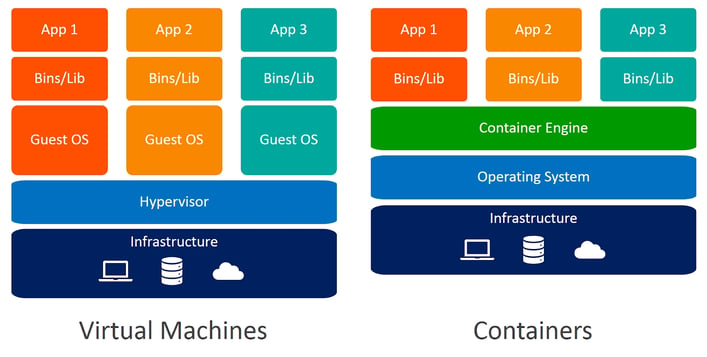
Nowadays there is a strong tendency to use “software-defined” approaches in everything, including the computer industry itself. We use virtual machines, virtual switches, virtual networks - all of those things are abstractions, exist in software. This is applicable for variety of purposes:
- Software development - for testing purposes
- Security research
- Fast prototyping
Docker is a virtualization technology which packs software into “containers” which runs in the docker engine. It is slightly different from the Virtual machines technology because it requires only the minimal components to be present in a container to make it running. Technically docker acts as a “runtime server”.
A container may allow to run a wide range of OS-dependent software inside a unique host - the docker engine. Containers have ports, services and disk mapping and they run inside internal networks to the docker engine. Therefore we can simulate realistically an entire infrastructure using a unique docker engine, a container simulating an ATC infrastructure component (Radar, ATC personnel station etc …)
- Containers - i.e. software and its environment
- Network[s] - software-defined network, fully isolated or connected to physical network
- Services - ports for software.
- Volumes - software-defined informational storage.
For further information about docker, see here.
Docker-based virtual ATC infrastructure
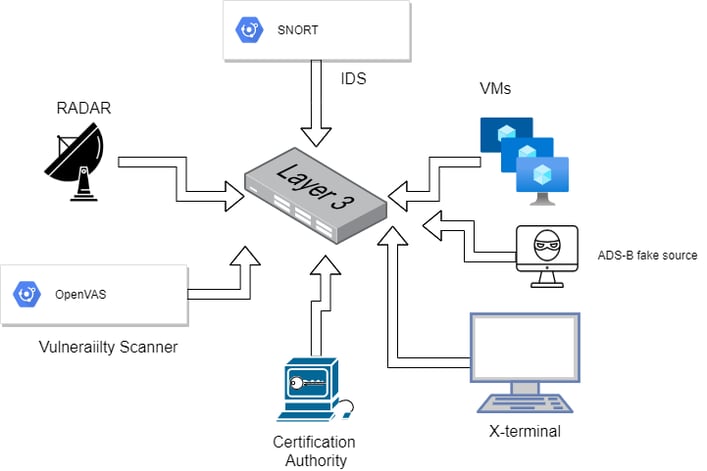
The BA&D is entirely based on docker. This approach adds to infrastructure an unprecedented flexibility, and ability to deploy many scenarios in a fairly simple and universal way! The BA&D uses the following components:
- A virtual simple ATC Controller Working Position CWP (in the full version even a real and fully functional ATC system with professional CWP positions in consoles - it is used for displaying the airplanes landing or taking-off or approaching the airport
- Radar data distribution server
- Radar data source (emulator)
- Attacking station
- Software switch
- Virtual DHCP server
Picture5 : BA&DACS components
Picture 5: all components - any OS and even switch itself - are simulated by a software .
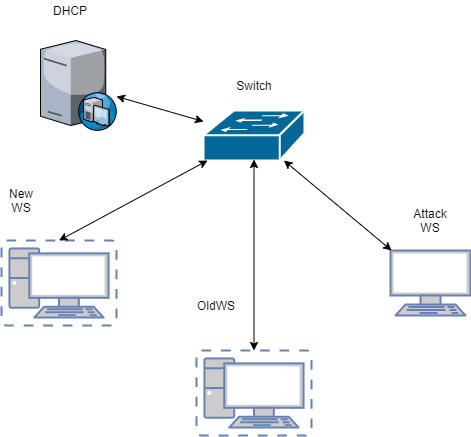
BA&D Virtual network Topology
Picture 6 represents a sample network topology - as mentioned previously, it\'s all software-based - even Layer 3 switch. The “case” - i.e. a particular scenario - can be deployed as a single file.
Virtual networks in management GUI. Every network could be fully isolated or connected to enterprise LAN, containing VLANs etc.
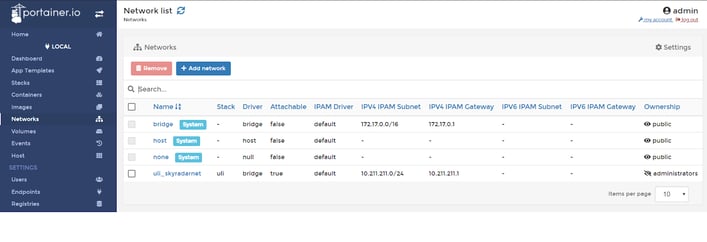 Picture7 : docker components (networks)
Picture7 : docker components (networks)
BA&D Interface with users
The primary way to interact with the BA&D for the students is via the computer shell . The shell contains all the commands needed for the simulator to operate.
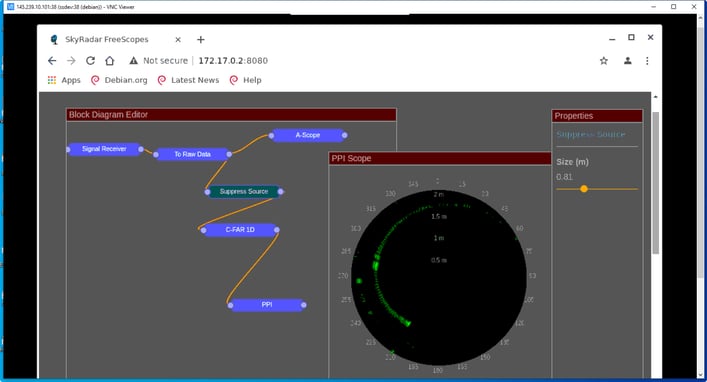
Picture 8: radar view (pedagogical approach including the block diagram)
Picture 9: shell access to the BA&D
Each attack can therefore be simulated via a special command in the shell. The cyber-defenses are also to be set via the same shell but, this time, from a cyber-defender perspective. (see Picture 9)
Effects of attacks can be viewed by connecting to FreeScopes and seeing either a denial-of-service, or the wrong data “ghosts planes everywhere”.. (see Picture 8)
Attack Simulation Scenario
For the moment the BA&D proposes a unique attack scenario :
⇒ Step 1) the attacker uploads a malware (Trojan) to a website and sends an SMS to an ATC employee, mimicking a legitimate request from the ATC IT infrastructure to download an update. The employee carelessly operates the requested task and launches the malware on their machine, resulting in opening a shell from their machine to the remote attacker.
The ATC employee is perfectly unaware of this situation.
⇒ Step 2) Having administrative rights on a machine of the network, the attacker decides to attack a redis server on the same network. The attackers gain shell access to the Redis machine.
⇒ Step 3) The attacker runs a bruteforce attack from his limited shell account from Redis to get administrative rights and break the root’s password. This allows the attacker to maliciously forge data. As a result the ATC controllers see “ghost planes\'\' over the radar and must quickly assert about the situation.
⇒ Step 4) Finally the attacker ( which may not have obtained its goals whatever they were ) decides to create a massive DoS , potentially also to mask his acts, and use DHCpig and eventually other DoS tools inside the ATC network.
The BA&D allows to simulate the attack scenario from step1) to step4) and will also provide a way to understand how this attack could have been prevented for each of the steps.
Stay tuned! with the forthcoming articles on cyber-defense in ATC, or sign up for a free two-week testing of our Breach, Attack & Defense Simulator:
About the Authors
Martin Rupp is a cryptographer, mathematician and cyber-scientist. He has been developing and implementing cybersecurity solutions for banks and security relevant organizations for 20 years. Currently he is researching attack scenarios and the role of AI in ATC cyber-security.
Peter Smirnoff has a long experience in Cryptography, both in industry and research. Peter has worked on the Windows Crypto API, OpenSSL, digital signatures, X 509 Certificates etc. He has profound implementation experience with PKCS-11 smart-cards as well on Linux and Windows platforms.
Ulrich Scholten is a founder of SkyRadar. As a research associate at the Karlsruhe Service Research Institute, he researched network effects, emergence and control mechanisms in platforms and distributed cloud scenarios. He holds several patents in radar technology and the Internet of Things and a PhD in Cloud computing.
References and Further Reading
- Gartner Top Security and Risk Trends for 2021 (April 2021)
- Read more about Cybersecurity for ATSEP and AVSEC (2019-today), by Dawn Turner, Martin Rupp, Peter Smirnoff, Ulrich Scholten and Dennis Vasilev.
- More articles on Cryptography, Key Blocks and Key Management (2018 - today), by Martin Rupp
- Articles on the protection of critical platforms and strategic response (2017 - today), by Ulrich Scholten and Stefan Hansen
- Articles on Key Management and HSMs (2017 - today), by Peter Smirnoff
- Articles on Digital Signing, the eIDAS standard, cyber-security and ATSEP qualification (2016 - today), by Dawn M. Turner